Proxmox as a hypervisor does - at least not in the default configuration - prevent QEMU VMs from using any IP they wont. If you use the default bridged networking setup, every Virtual Machine can use any IP it wants.
This is probably not a problem in internal environments where you are the only Administrator and also User and control every VM and the whole network.
When you start allocating resources on your Proxmox Server to outside collaborators or customers, you probably want to limit the IP-Addresses that each VM can use. If you are Colocation Provider monitors IP-Traffic and limits IPs to certain MAC-Addresses this setup can become crucial for your business-stability.
Practical Example
Let's say you rent a server from a provider along with a subnet (11.234.192.0/24), that means that you can freely use all the IPs in the range 11.234.192.1 to 11.234.192.255 for your Proxmox Host. You would configure your Host like usual, adding the IPs. Now, when you provision a new VM, you add a single IP to the config: 11.234.192.30. When the VM boots for the first time, the IP is added to the `/etc/network/interfaces` file. Now, the customer can edit that file and change the IP to any he wants to, maybe the IP of your website VM that's running on the same host. Outgoing and Incoming packets would now be routed to either one of these VMs, which creates unpredictable behavior and certainly a security issue.
Setup
First, we need to found out the name of the network interface the VM uses. This is usually `net0`, but you can quickly check it in the Hardware tab of the VM.
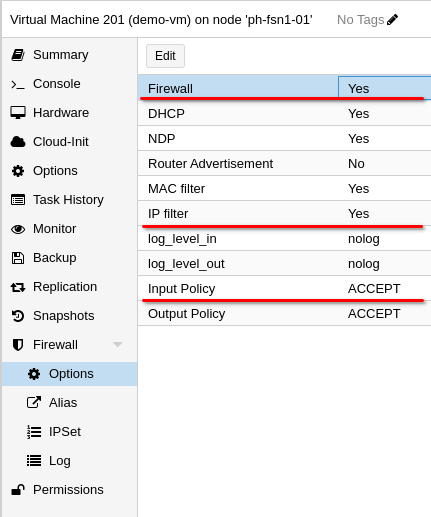
Next, we navigate to the Firewall > Options page, we enable the firewall and also enable IP filter, which is the crucial part. Make sure to change Input and Output Policy to ACCEPT, so traffic can pass freely.
At last, we go to Firewall > IPSet and create a new IP set. The name needs to be like `ipfilter-net0`, where `net0` is the name of the network interface you've saved from before.
Next, add the IP you want to limit the VM to to the newly created IPSet, which will enable the filter.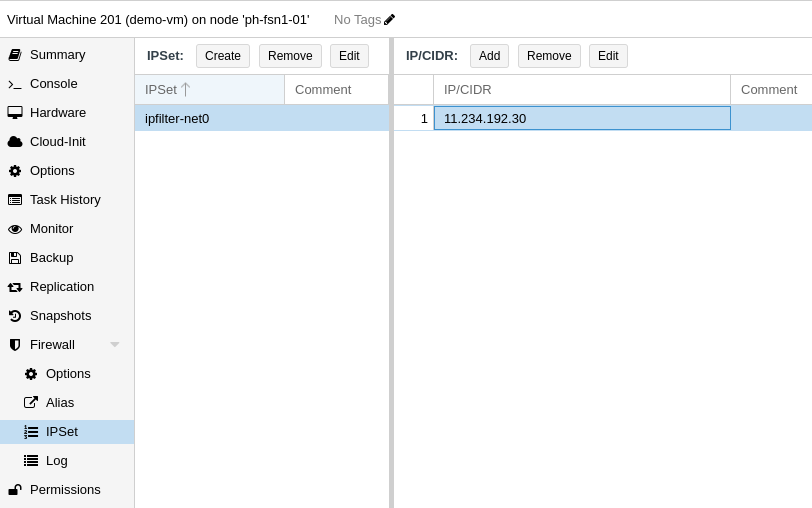
IPSet Rules in the ProxmoxCP
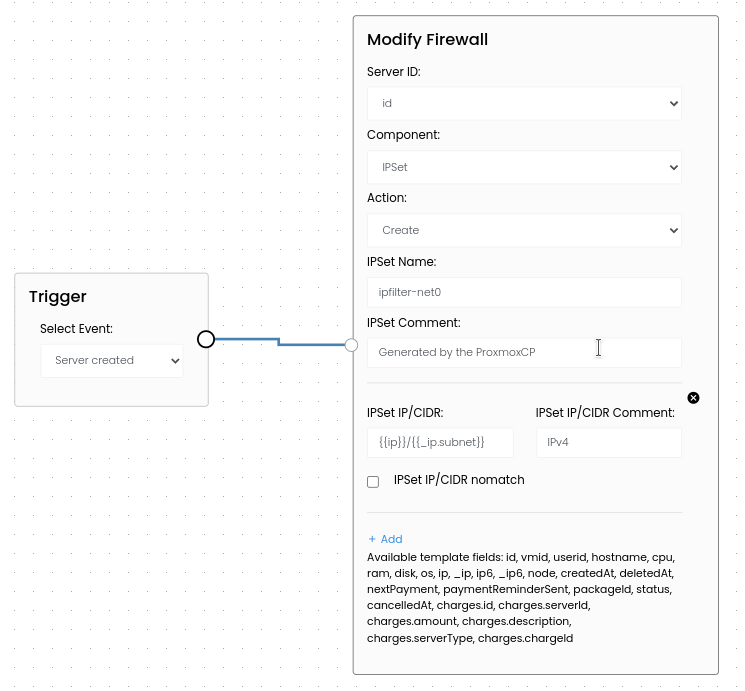
In the ProxmoxCP, you can make leverage the Event System to create an anti IP-Spoofing rule, which will get automatically created when a new server is created.
We use the Server created event to trigger the "Modify Firewall" Action, which can create or update an IPSet. We use the templating Syntax to add the IP and Subnet.
This way, whenever a server get's created, the rules get also applied automatically.
Conclusion
In this post, we've learned what IP Spoofing is and why it might be not beneficial or even dangerous in your environment. But we've also look at what we need to do in order to mitigate this thread.